Top 7 Challenges For Cloud Browser Isolation
Top 7 Challenges For Cloud Browser Isolation
Cloud Browser Isolation Definition
| Remote browser services redirect the act of internet browsing from the end user’s desktop into a remote server, either on-premises in the demilitarized zone (DMZ) or delivered as a cloud-based service. The user still browses the public internet, but attacks are kept isolated in the remote browser sessions. |
80% of web attacks are browser-born
Browsing the internet opens every business to significant risk. 80% of web attacks are browser-born attacks that target users via malicious URLs.
A malicious URL is a web page that contains malicious code which runs on your desktop while you’re browsing that particular page. Malicious URLs can harm corporate and privately-owned computers alike by encrypting all the files or stealing personal data. When it comes to businesses and large corporations such as clinics, hospitals, banks, educational establishments and governmental agencies, the effect of this risk is much more devastating and can have cooperation-wide repercussions.
A single corporate user who browses the internet may, unintentionally, place an entire organization, along with its most sensitive corporate assets, at great risk. Multiply that single user by tens, hundreds or thousands of users and the risks that organizations face today by allowing their employees to surf the internet are practically incalculable.
Why this happens:
1. Browser vulnerabilities while browsing legitimate web sites such as Facebook, Google, Salesforce Office 365 & malicious websites which are designed to attack their visitors.
2. Emails received containing malicious URLs
3. Files downloaded from the internet
4. Browser born vulnerabilities invoked from applications i.e. Adobe reader, flash, java and office.
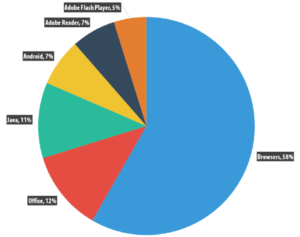
Distribution by Type of Attack on Enterprise Users – Source: Kaspersky Lab
Security protection products are not enough against malicious code. It is only a matter of time before the enterprise network becomes compromised.
Top 7 Foundations For Any Cloud Browser Isolation
Solution Maximizing the benefits of a secure browsing solution requires the installation of a system that delivers a full range of key capability and usability features. The following, in particular, should be considered must-have features for secure browsing solutions undergoing evaluation for deployment in any organization:
1.Browsing Policy Enforcement: Virtually every enterprise on the planet has implemented policies that dictate employees’ activities and actions regarding internet access. These policies are designed, at least in part, to help prevent the occurrence of browser-based security breaches. Many organizations, however, do not actively enforce the policies, rendering the policies effectively worthless in providing a form of defense. A secure browsing solution should enable and facilitate the universal enforcement of organizational browsing policies.
2.Seamless User Experience: From the user’s perspective, secure browsing should be transparent. The experience should be identical to using a desktop-based browser. It is particularly crucial that the secure browsing solution enable personalization in a single browser environment.
The challenge is isolating malicious code out of businesses, while maintaining user’s browsing experience
3.User Identity Protection and Management: The solution should anonymously shadow user’s protection.
4.Browsing Performance Utilization: Though browser performance can suffer with some remote solutions, a secure solution should ideally enable performance that is on par with desktop-based browsers. Some secure browsing solutions can even enhance browsing performance by facilitating a range of cloud and on-premise options for accessing different websites securely. The best, safest platform should be automatically determined for URLs, users and location-based prioritization and scheduling management.
5.Cloud Internet Browsing: Maximum efficiency and user productivity are facilitated with solutions that enable internet browsing on any cloud system or data center.
6.Browser Compatibility: The solution should enable the use of a single browser for all different applications and URLs.
7.Regulatory Compliance: The ability to maintain 100 percent separation between the internet and sensitive enterprise data is a good policy for all companies, and a regulatory necessity for many companies.
Read more how Cigloo Cloud Secure Browsing can allow your organizations to maintain the necessary security levels of your business, without fear of cyber attacks through web browsers, email links and files downloads.